PHOTO/Courtesy
High-ranking business executives have equally unhealthy password habits as many other internet users do, according to new research by NordPass. Business owners, CEOs, and other C-suite executives have “123456,” as their passwords, despite the many warnings from cybersecurity experts.
NordPass, a password manager for both business and consumer clients, in partnership with independent researchers specializing in the analysis of cyber incidents, compiled an extensive list of top passwords used by top-level executives.
The business executives showed a visible trend to use easily hackable passwords that mainly include sequence combinations of numbers or letters.
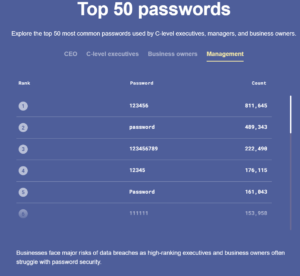
These include but are not limited to “1q2w3e,” “12345,” “11111,” and “qwerty.” “123456” was found to be the most preferred password , with over 1.1 million times usage. The word “password” came second in the list of preferences. It had over 700 thousand users.
The research suggests that top-level executives also extensively use names or mythical creatures as an inspiration when creating passwords. Among the most popular are “dragon” and “monkey.” The most widely chosen names used in passwords are “Tiffany,” “Charlie,” “Michael,” and “Jordan,” which may or may not hint at the legendary basketball player.
This research was conducted in partnership with independent researchers who analyzed over 290 million data breaches worldwide. They grouped passwords according to job title and industry — among many fields affected, technology, finance, construction, healthcare, and hospitality were shown to experience the most security incidents.
Amidst the countries that experienced breaches examined in this study, France and the United Kingdom were listed among the most breached, accounting for 200 million and 600 million passwords leaked respectively.
The analysis findings demonstrate that business owners, C-suite, and other high-ranking executives, expected to be more conscious about their security online than the average internet user, have similarly poor password habits. This significantly increases the risks of cyberattacks at both the person and company level.
Last year, NordPass presented similar studies, delving into the Top 200 Most Common Passwords people use online and those of Fortune 500 companies. Interestingly, the comparison of research shows that business executives are as likely to use easy-to-crack passwords as general internet users: “123456” and “123456789” rank in the top five among both audiences.
“It is unbelievable how similar we all think, and this research simply confirms that — what we might consider being very original, in fact, can place us in the list of most common,” says Jonas Karklys, the CEO of NordPass.
“Everyone from gamer teenagers to company owners are targets of cybercrimes, and the only difference is that business entities, as a rule, pay a higher price for their unawareness.”
The IBM report reveals that in 2021, the average global cost of a data breach reached 4.24 million USD, which is 10% more compared to 2020. The attacks that happen due to compromised credentials cost even more at 4.37 million USD and account for 20% of all breaches.
According to Karklys, people can avoid many data breaches by following simple steps to improve password security:
- Deploy a password manager. Password managers allow you to store all the passwords in end-to-end encrypted digital storage locked with a single keyword for the most convenience. Most password managers have additional features to check passwords’ strength and automatically generate unique passwords. For organizations, they can come in handy when sharing passwords with employees or managing their access.
- Introduce cybersecurity training. Since simple human mistakes remain the leading cause of data breaches, it is worth investing in cybersecurity training sessions for employees. Starting from the basics might be a good idea given that people have different technology background levels.
- Enable multi-factor authentication. Known as MFA, it serves as an extra layer of security. It is an authentication method that uses two or more mechanisms to validate the user’s identity – these can be separate apps, security keys, devices, or biometric data.



